Audit of Natural Resources Canada (NRCan) Cyber Security (AU1703)
Audit Branch
Natural Resources Canada
Presented to the Departmental Audit Committee (DAC)
March 30, 2017
This report contains information severed in accordance to the Access to Information Act.
TABLE OF CONTENTS
- EXECUTIVE SUMMARY
- INTRODUCTION
- BACKGROUND
- FINDINGS AND RECOMMENDATIONS
- Cyber Security Policy Framework
- Cyber Incident Management and Resilience (Information has been severed in its entirety)
- Cyber Security Risk Management
- Cyber Security Training and Awareness
- Cyber Security Performance Measurement and Reporting
- Cyber Security Funding/Resource Allocation (Information has been severed in its entirety)
- APPENDIX A – AUDIT CRITERIA
EXECUTIVE SUMMARY
INTRODUCTION
In delivering its mandate to enhance the responsible development and use of Canada’s natural resources and the competitiveness of Canada’s natural resources products, Natural Resources Canada (NRCan) is heavily reliant on various information technology (IT) systems and processes which are primarily managed using a decentralized approach through many regional offices and laboratories across the country. Securing these IT systems from cyber threats is essential to maintaining the confidentiality, integrity and availability of the information within the systems thereby allowing the Department to deliver on its mandate. In addition, with Shared Services Canada (SSC) now responsible for securing the underlying IT infrastructure on which NRCan IT systems operate, there are additional challenges to coordinate cyber security activities with SSC to help ensure IT systems are holistically protected from cyber threats.
Cyber security governance at NRCan is primarily delivered through the Information Management and Technology Committee (IMTC). IMTC provides recommendations to the Business Transformation Committee (BTC), the Department’s primary decision making body for IMT matters. Some Sectors also have IM/IT committees, which would also include cyber security considerations for the Sectors. In addition, a Project Management Board (PMB) has been created to manage the delivery of NRCan’s Cyber Security Action Plan (CSAP), a three-phased plan developed to address cyber security risks and compliance requirements.
The objective of the audit was to assess whether NRCan has an effective management control framework in place to meet policy requirements; identify vulnerabilities and incidents; and mitigate risks related to cyber security.
STRENGTHS
The following strengths were noted during the audit:
- The Cyber Security Action Plan (CSAP) was developed in collaboration with the Sectors, and is aligned with the departmental IT plan, compliance requirements, and incorporates identified departmental cyber security risks;
- Members of the IMTC interviewed were supportive of the process through which the CSAP was developed, and of the priorities identified in the plan;
- Integration and collaboration between NRCan and SSC is improving, which increases the effectiveness of the CSAP and cyber security in general;
- The recently developed Security Assessment and Authorization Directive is aligned with central agency guidance and takes a risk-based approach designed to support an efficient allocation of resources; and
- Numerous CSAP status updates and reports have been issued to provide senior management with regular updates on the status of the CSAP.
AREAS FOR IMPROVEMENT
[This information has been severed]
AUDIT CONCLUSION AND OPINION
Although some elements of the cyber security management control framework are in place, including oversight committees at the departmental and Sector levels [This information has been severed].
STATEMENT OF CONFORMANCE
In my professional judgement as Chief Audit Executive, the audit conforms with the Internal Auditing Standards for the Government of Canada, as supported by the results of the Quality Assurance and Improvement Program.
Christian Asselin, CPA, CA, CMA, CFE
Chief Audit Executive
March 30, 2017
ACKNOWLEDGEMENTS
The audit team would like to thank those individuals who contributed to this project and particularly employees who provided insights and comments as part of this audit.
INTRODUCTION
Canadians trust that the federal government will ensure the integrity of their personal and corporate information in the delivery of services. However, government information technology (IT) systems have become an attractive target for malicious attacks by both international and domestic criminals. Foreign countries and other entities are using the Internet to steal classified information, including government and trade secrets, and commercially sensitive and private information from business systems. These ‘cyber-attacks’ are often characterized as inexpensive, easy, effective, and low risk, and are delivered through an ever growing and evolving set of tools and techniques. Cyber security is about mitigating these threats and reinforcing the safety of Canadians online.
In delivering its mandate to enhance the responsible development and use of Canada’s natural resources and the competitiveness of Canada’s natural resources products, Natural Resources Canada (NRCan) is heavily reliant on various IT systems and processes, which are primarily managed using a decentralized approach through many regional offices and laboratories across the country. These systems enable the Department to conduct science across natural resource Sectors in 18 major satellite Science and Technology Centers, laboratories, and facilities across Canada. Securing these IT systems from cyber threats is essential to maintaining the confidentiality, integrity, and availability of the information within the systems, thereby allowing the Department to deliver on its mandate.
In addition, the creation of Shared Services Canada (SSC), in August of 2011, increased the complexity of managing cyber security as some functions continue to be the responsibility of NRCan while other functions have been transferred to SSC. As part of SSC’s mandate to consolidate, standardize, and streamline the delivery of email, data centres, and network services in the Government of Canada, the responsibility for NRCan’s IT Infrastructure was transferred to SSC along with that of 42 other departments. As a result of these changes, SSC became responsible for securing the underlying IT infrastructure on which NRCan IT systems operate. This requires NRCan to coordinate cyber security activities with SSC to help ensure IT systems are fully protected from cyber threats.
BACKGROUND
Cyber Security Governance
The NRCan Chief Information Officer (CIO) is accountable via the Assistant Deputy Minister Corporate Management and Services Sector (ADM CMSS) to the Deputy Minister for the overall cyber security direction and performance; however, considering NRCan’s decentralized model, the CIO does not have oversight over IT resources within the Sectors [outside of the Chief Information Officer and Security Branch (CIOSB)]. As such, accountability for securing NRCan systems and data is shared between the CIO and Sectors.
While not all details related to cyber security roles and responsibilities have been defined, SSC is generally responsible for the cyber security of the IT infrastructure (email, networks, data centers and servers), while NRCan is responsible for the cyber security of the applications/systems and data residing on the IT infrastructure. Consequently, the CIO acts as a liaison with SSC to implement cyber security measures on the IT infrastructure managed by SSC, and works with the Sectors to implement cyber security measures on IT applications/systems and data managed by the Sectors.
The main governance body at NRCan for cyber security is the Information Management and Technology Committee (IMTC – formally known as the Information Management and Technology Project and Architecture Review Board - IMT-PARB), which is the Department's senior IMT management committee responsible for bringing a business focus to the IMT domain, including cyber security. IMTC provides recommendations to the Business Transformation Committee (BTC) as the Department’s primary decision making body for IMT matters. Some Sectors also have IM/IT Committee which would also include cyber security considerations for the Sectors.
A Project Management Board (PMB) has been created to manage the delivery of the Cyber Security Action Plan (CSAP). The CSAP PMB is supported by various project teams and working groups focused on various elements of the CSAP. The governance model is depicted below:
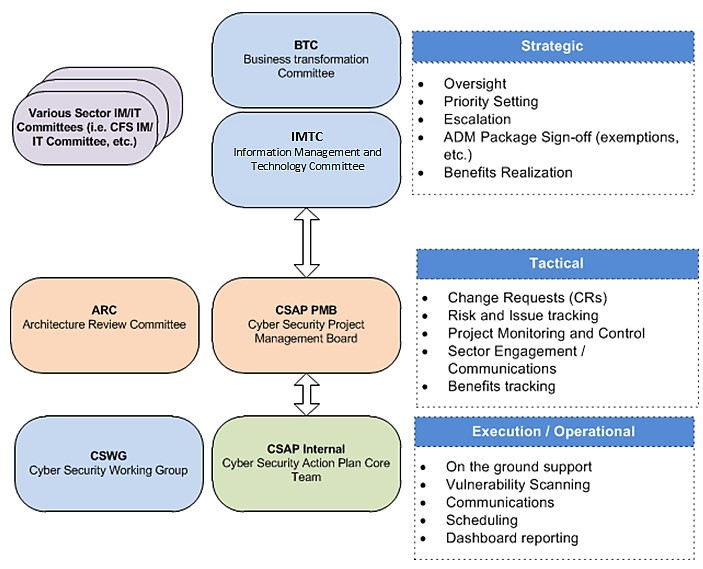
Text version
This figure illustrates the governance model employed by the Project Management Board for the delivery of Cyber Security Action Plan (CSAP). The board is supported by several project teams and groups focusing on various elements of CSAP. The governance Structure comprises of three components: strategic, tactical and execution/operational.
The strategic component of the governance consists of two committees, namely the Business Transformation Committee (BTC) and the Information Management and Technology Committee (IMTC), which are supported by other IM/IT committees. The roles and responsibilities of committees include providing oversight, setting priorities, escalation, sign-offs; as well as benefit realizations.
The second component providing tactical support encompasses two committees, Architecture Review Committee (ARC) and Cyber Security Project Management Board (CSAP PMB). These committees are responsible for overseeing and making technical decisions such as change requests, tracking of risks/issues, project monitoring and controls as well as engagements and communications with all sectors.
The execution/operational committee consists of the Cyber Security Working Group (CSWG) as well as the Cyber Security Action Plan Core Team (CSAP Internal). These groups provide ground support including vulnerability scanning, communication, scheduling and dashboard reporting.
An Audit of IT Governance was performed in 2015, which highlighted a number of findings that have a bearing on cyber security, including that the current IT governance model is decentralized, [This information has been severed].
Cyber Security Action Plan (CSAP)
In 2015 NRCan developed a Cyber Security Action Plan (CSAP), divided into three distinct phases as follows:
- Phase 1 was completed in October 2015 and focused on mitigating immediate risks in the short term. Activities included an email phishing testing and awareness campaign and the implementation of controls for public-facing systems.
- Phase 2 was initiated in November 2015 with a target completion date of March 2017 and is focused on documenting strategies to mitigate high risks in the medium-term. [This information has been severed]
Cyber Security Policy Framework
NRCan has policy instruments that are relevant to cyber security, including the following:
- NRCan Departmental Security Policy (May 2011) – serves to establish a framework for the departmental security program, including physical security, information security, personnel security screening and IT security. It provides the foundation for IT security controls including: Planning, Architecture, Certification and Accreditation, Compliance to Policies, Directives and Standards, User Awareness and Accountability, Electronic Storage and Transmission of Information, Monitoring, and Incident Response and Recovery.
- NRCan Directive on Security Assessment and Authorization (SA&A) (June 2016), which provides the foundation for departmental SA&A processes.
Government-wide, there are also policy instruments and guidance that are relevant for cyber security, including the following:
- The TBS’ Policy on Government Security (PGS) and related Security Policy Implementation Notices (SPIN).
- The TBS’ Management of IT Security (MITS) Standard.
- The Communications Security Establishment’s (CSE’s) Top 10 IT Security Actions to Protect Government of Canada Internet-Connected Networks and Information (ITSB-89 Version 3).
- The CSE’s IT Security Risk Management Guidance (ITSG-33).
- The Government of Canada’s Cyber Security Event Management Plan (GC CSEMP).
Based on the ever-evolving cyber threat landscape and the complexities surrounding NRCan’s governance model for cyber security, the Audit of NRCan Cyber Security was included in the Department’s Risk-Based Audit Plan, approved by the Deputy Minister on March 10, 2016.
AUDIT CONSIDERATIONS
A risk-based approach was used in establishing the objectives, scope, and approach for this audit engagement. [This information has been severed]
AUDIT OBJECTIVE
The objective of the audit was to assess whether NRCan has an effective management control framework in place to meet policy requirements, identify vulnerabilities and incidents, and mitigate risks related to cyber security.
Specifically, the audit assessed whether:
- There are adequate policies, plans and resources in place for the effective management of cyber security;
- Effective cyber security processes are in place to mitigate risks; and
- There is effective oversight of cyber security through performance measurement and monitoring.
SCOPE AND METHODOLOGY
The audit examined the activities of CIOSB and the Sectors in managing Cyber Security and securing NRCan systems. The scope of the engagement included an assessment of the controls in place to support the Department to identify, prevent and recover from a cyber security attack including:
- the policy framework;
- procedures dealing with risk and vulnerability management;
- processes for handling incidents, resiliency to cyber-attacks, security assessments, operational controls over network access and protection; and
- overall staff awareness.
The audit also considered the results of recent audits completed in the areas of IT Governance and Physical Security.
The audit included liaison and communication between SSC and NRCan related to cyber security processes, but excluded a direct review of SSC operations and how it secures the IT infrastructure on which NRCan systems reside. Therefore, this audit provides partial assurance on cyber security due to the exclusion of SSC.
The conduct phase of this audit was substantially completed in December 2016.
The audit was performed with the assistance of an external contractor with extensive experience in the field of IMT and Cyber Security within the Government of Canada.
The audit methodology is based on the TBS Policy on Internal Audit and the Government of Canada’s Internal Audit Standards, and included the following:
- Interviews with key personnel with respect to the Department’s cyber security activities and related models;
- Review of key documents, including the Cyber Security Action Plan (CSAP), cyber security-related committee structures, meeting minutes, and relevant policies and directives; and
- A detailed examination of cyber security processes related to incident management.
CRITERIA
The audit criteria were primarily developed using relevant TBS and NRCan policies, procedures, and directive, including the TBS Policy on Government Security and the Management of IT Security (MITS) Standards.
Please refer to Appendix A for the detailed audit criteria.
FINDINGS AND RECOMMENDATIONS
CYBER SECURITY POLICY FRAMEWORK
Supporting Finding
[This information has been severed]
Supporting Observations
NRCan’s approved policies related to cyber security currently consist of the following:
- NRCan Departmental Security Policy (May 2011)
- NRCan Directive on IT System Development (January 2015)
- NRCan Directive on Security Assessment and Authorization SA&A (June 2016)
RISK AND IMPACT
[This information has been severed]
RECOMMENDATION
[This information has been severed]
MANAGEMENT RESPONSE AND ACTION PLAN
[This information has been severed]
CYBER INCIDENT MANAGEMENT AND RESILIENCE
Supporting Finding
[This information has been severed]
Supporting Observations
[This information has been severed]
RISK AND IMPACT
[This information has been severed]
RECOMMENDATIONS
[This information has been severed]
MANAGEMENT RESPONSE AND ACTION PLAN
[This information has been severed]
CYBER SECURITY RISK MANAGEMENT
Supporting Finding
[This information has been severed]
Supporting Observations
Under the Government of Canada’s Policy on Government Security, cyber security risk management is mainly conducted through a process called Security Assessment and Authorization (SA&A). SA&A requires that cyber security controls be identified early in an IT system’s lifecycle, so that they can be built into the design of systems and implemented before the system is granted an authority to operate. This helps ensure that a new system does not introduce cyber/IT security risks to the overall IT infrastructure, which would impact all systems and data using that same IT infrastructure.
The responsibility to perform SA&A activities on the NRCan IT infrastructure (email, networks, servers and data centers) lies with SSC, while in NRCan’s decentralized environment, system owners within the Sectors are responsible for providing evidence that they have designed and implemented adequate security controls based on the sensitivity of their systems. The CIOSB then certifies that controls are in place and grants systems a security authority to operate. SA&A roles and responsibilities are specified in the NRCan Directive for SA&A, which was issued in June 2016 and sets the foundation for cyber/IT security risk management activities on NRCan systems.
[This information has been severed]
RISK AND IMPACT
[This information has been severed]
RECOMMENDATIONS
[This information has been severed]
MANAGEMENT RESPONSE AND ACTION PLAN
[This information has been severed]
CYBER SECURITY TRAINING AND AWARENESS
Summary Finding
[This information has been severed]
Supporting Observations
The Department has been providing some cyber security-related training and awareness activities, including an E-Learning module on security and privacy and other related topic, basic awareness email broadcasts, and an e-mail phishing awareness campaign, which sent simulated phishing emails to employees to train them in recognizing phishing emails. A one-day session on how to develop secure applications was also provided to developers and scientists in October 2016.
[This information has been severed]
RISK AND IMPACT
[This information has been severed]
RECOMMENDATION
[This information has been severed]
MANAGEMENT RESPONSE AND ACTION PLAN
[This information has been severed]
CYBER SECURITY PERFORMANCE MEASUREMENT AND REPORTING
Summary Finding
Cyber security performance measures and reporting exist for the Cyber Security Action Plan, but there are currently no performance measures tracked and reported to senior management on the overall state of cyber security at NRCan.
Supporting Observations
Cyber-security performance measurement and reporting currently consists of CSAP dashboards and other CSAP-related project artefacts that report on the health of the CSAP as a project. The dashboards report on the status of each CSAP activity, project risks and issues, as well as the overall CSAP project progress.
It was noted, however, that there are currently no performance measures tracked and reported to senior management on the state of cyber security at NRCan. A Performance Measurement Framework for cyber security has not yet been developed that would go beyond tracking CSAP activities to track the progress of achieving the expected outcomes of the cyber security program. It would require establishing a baseline of the current level of cyber security and then tracking the impact of activities [This information has been severed]
RISK AND IMPACT
[This information has been severed]
RECOMMENDATION
- The Chief Information Officer (CIO) should develop performance measures on the state of cyber security at NRCan and report results to senior management on a regular basis.
MANAGEMENT RESPONSE AND ACTION PLAN
Management agrees. In response to recommendation 7:
Corporate Management and Services Sector (CMSS) provides quarterly reports to the Executive Committee on cyber security. Revised performance measures, which are aligned with the Information Management and Technology (IMT) Strategy and Departmental Security Policy (DSP) will be identified and included in the management monitor. [This information has been severed]
Position Responsible: Chief Information Officer
Timing: June 30, 2017
CYBER SECURITY FUNDING/RESOURCE ALLOCATION
Supporting Finding
[This information has been severed]
Supporting Observations
[This information has been severed]
RISK AND IMPACT
[This information has been severed]
RECOMMENDATIONS
[This information has been severed]
MANAGEMENT RESPONSE AND ACTION PLAN
[This information has been severed]
APPENDIX A – AUDIT CRITERIA
The audit criteria were primarily developed using relevant Treasury Board Secretariat and NRCan policies, procedures, and directive, including the TBS Policy on Government Security and the Management of IT Security (MITS) Standards.
| Audit Sub-Objectives | Audit Criteria |
|---|---|
| Audit Sub-Objective 1: To determine whether there are adequate policies, plans and resources in place for the effective management of cyber security. |
1.1 The policy framework is adequate to ensure required cyber security controls are consistently applied throughout the organization. |
|
1.2 Roles and responsibilities related to cyber security between the Sectors, CIOSB and SSC are clearly defined and communicated. |
|
|
1.3 A cyber security plan has been developed in alignment with the IT plan to address cyber security risks and compliance requirements (CSE Top 10, SPIN). |
|
|
1.4 There is an effective process in place to determine the level of resources required to ensure cyber security risks are managed effectively. |
|
| Audit Sub-Objective 2: To determine whether there are effective cyber security processes in place to mitigate risks. |
2.1 There is an effective process to identify, analyze, contain and recover from incidents in a timely manner. |
|
2.2 There is an effective process to mitigate cyber security risks in IT systems in a timely manner. |
|
|
|
| Audit Sub-Objective 3: To determine whether there is effective oversight of cyber security through performance measurement and monitoring. |
3.1 A performance monitoring process is in place to evaluate CSAP performance and the evolution of cyber security risks. |
Page details
- Date modified: